|
Kingston IronKey S1000
For when you need a rugged, heavy-duty USB key that truly protects your data
(by Conrad. H. Blickenstorfer)
This article is about the encrypted, secure IronKey S1000 USB flash storage key from Kingston Technology. From what we can tell, the IronKey S1000 line offers the highest level of encryption available in this market. These keys are geared toward governmental agencies at the city, state and federal level who need to be in compliance with FIPS 140-2 Level 3, as well as to civilian and defense contractors who are doing business with the government. The article also touches on the history of USB keys, the need for security, applying security technologies and certifications, and, of course, about the Kingston IronKey S1000 itself.

Almost two decades ago I was at a mobile computing conference, and the goodie bag included this strange thing about the size of a Swiss Army pocket knife. It had a cap on it and under the cap was a USB connector. I stuck it into my IBM Thinkpad and after a bit of milling, Windows 2000 informed me that I now had an 8MB external disk. I could drag files from it to me Thinkpad, and from the Thinkpad to that external storage volume on what was the first USB key I had ever seen.
I was blown away. The USB interface was still new and its promise largely unfilled. There were a few peripherals here and there that used USB, and that was it. But here was a this small, handy little thing that was like an external hard disk but plugged right into a USB port. This had to be the start of something big. After the session I told the conference organizer that I considered that giveaway the biggest thing of the entire conference. He didn't seem interested.
USB flash drives, of course, went on to be a huge business that changed the industry, and how we use computers. Hundreds of millions are sold every year.
USB Flash drives — irreplaceable technology with some issues
That said, USB flash drives are not without problems. As is the case with other types of flash memory storage, the number of write/erase cycles of USB drives is limited. USB drives usually do not have write protection. USB keys can get bent at the insertion point, which can lead to failure. And like small storage cards, USB keys are all too easily lost.
Perhaps most importantly, flash drives present security risks. If stolen, data can simply be read from the USB key. A study looking into security aspects of USB drives (see here) showed that data loss due to missing USB keys is staggering, and that stolen USB keys are a primary source of data breaches. The study also found that most organizations:

- do not provide approved, high quality USB keys,
- do not have policies on acceptable use of USB keys,
- do not mandate and manage the use of secure USB keys,
- do not encrypt sensitive data on USB keys,
- do not scan USB drives for virus or malware infections, and
- do not actively enforce acceptable USB key use policies.
And this despite the majority of respondents stating that USB key encryption makes sense. And that USB keys improve the efficiency of IT operations.
Quite obviously, USB drives are hugely popular despite having some issues, and that popularity is unlikely to abate anytime soon. Some technical issues have been resolved over the years, USB drives don't only come with different capacities but also at different levels of quality, and users have accepted the possibility of loss as an acceptable risk.
But what about data security? Misplacing or losing a USB key, or having one stolen, can have potentially devastating consequences.
Enter secure USB drives
The obvious answer to USB key security issues is to concentrate on reasonable, effective solutions. And that means protecting the data residing on USB keys. This could potentially be done with physical means, like having a strong enclosure and a physical lock. That, however, would not be very practical, and virtually any physical lock can be defeated. So the industry decided on access authentication and data encryption instead. Let's consider:
Relatively simple pin or password access can be remarkably effective, as evidenced by recent cases where Apple claimed it was unable/unwilling to help the government breaking into standard iPhones. Sure, it would be relatively easy to crack a four or even six number pin, but modern authentication systems will lock up after so and so many attempts. Add to that hardware-based encryption where data is scrambled so thoroughly that it becomes impossible to read without legitimate descrambling, and you have pretty bulletproof security.
The government has figured that out for quite some time and documented data security procedures and requirements in their Federal Information Processing Standard 140.
What's FIPS 140-2? And AES and XTS?
FIPS stands for Federal Information Processing Standard. 140-2 refers to publication 140-2 "Security Requirements for Cryptographic Modules" (see here). This is a standard that "specifies the security requirements for a cryptographic module utilized within a security system protecting sensitive information in computer and telecommunication systems." There are four security levels, where:
- Level 1 only requires the presence of a cryptographic module.
- Level 2 requires the addition of tamper-evidence like a coating, seal or lock. It also requires "role-based" user authentication (i.e. having admin access or something similar) and a trusted operating system.
 - Level 3 requires "identity-based" user authentication (i.e. a personal code or password), a response to unauthorized access attempts, such as warnings and irretrievable erasing of all data. This so happens to be what the IronKey S1000 offers.
- There's also a Level 4 that adds physical security and environmental sensing that would not be practical for a USB key.
There's more, however. Hardware encryption comes in many varieties. In computer data storage, an encryption system will usually scramble 128-bit or 256-bit blocks of data in one way or another. AES (Advanced Encryption Standard) is an often used algorithm that also comes in several varieties or modes. Here, a mode called XTS ("cypherteXT Stealing") offers several advantages and is considered desirable in storage encryption and security.
Why do I mention all of this highly technical stuff? Because the elegant looking Kingston IronKey S1000 shown in the picture on top of this article provides 256-bit AES hardware-based encryption in XTS mode, and adheres to FIPS 140-2 Level 3 validation with its own hardware encryption chip.
The Kingston IronKey S1000
 Now we're finally getting to the actual subject of this review, Kingston's IronKey S1000. The picture to the right shows three USB keys that couldn't be more different. Now we're finally getting to the actual subject of this review, Kingston's IronKey S1000. The picture to the right shows three USB keys that couldn't be more different.
On the far right is what one finds inside a more or less generic modern 16GB USB key.
In the middle is one of the earliest USB keys I picked up at a 2002 trade show. It holds 16MB, or 1,000 times less than your typical contemporary key.
And then, to the left, the Kingston IronKey S1000 that holds 64GB, or 4,000 times as much data as its distant forebear, and in terms of security is like Fort Knox compared to a standard key's complete lack of protection.
IronKey started as an Internet security company with the help of US Homeland Security. The IronKey brand and technology was purchased by Imation, and subsequently by Kingston Technology where IronKey is now the top-of-the-line in encrypted secure flash drives.
The term IronKey is appropriate as the S1000 drive indeed looks like it's crafted from a solid block of metal. It isn't of course, but the electronics are inside a very solid anodized aluminum housing the walls of which look about 18 gauge in thickness. The casing is epoxy-filled and the device carries the equivalent of what we'd consider IP67 sealing, which means it is totally dustproof and can also handle immersion into water down to about three feet. Kingston says the S1000 conforms to IEC 60529 IPX8.
In terms of technology, the S1000 is at USB 3.0, which means a maximum read speed of 400 MB/s and a maximum write speed of 300 MB/s. The IronKey S1000 is FIPS 140-2 Level 3 validated and uses 256-bit AES XTS hardware encryption. The S1000 is available in capacities from 4GB to 128GB. We tested the 64GB version.
Using the IronKey S1000
How does one use the IronKey? That's a little different from using a regular USB key that just mounts as another disk and that's that. When you first insert a new IronKey S1000 into the USB port of a supported Windows, Mac or Linux system, a small 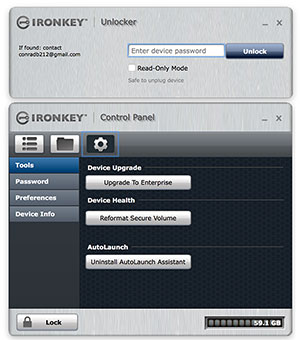 IronKey partition will mount (which means you'll need two free drive letters) and an IronKey app will auto-run the setup procedure where you set your password (at least four characters). IronKey partition will mount (which means you'll need two free drive letters) and an IronKey app will auto-run the setup procedure where you set your password (at least four characters).
Here you also determine whether the IronKey should self-destruct after ten failed access attempts, or if it should simply reset itself to factory condition after nuking all data. After making that decision, the IronKey will format itself for use.
Ever after, once you insert the IronKey, the IronKey partition will load and auto-execute, bringing up first the Unlocker and then the IronKey Control Panel which has three tabs.
The first shows a quick-start user guide, the second opens a window with your data, and the third brings up Preferences.
Preference tools include software upgrade to Enterprise level, reformatting the data volume, and uninstalling the auto-launch app. You can also change the password, set an auto-lock timeout, and an unlock message (like who to contact if the key is lost and found by someone).
Finally, there's device info that also links to helpful info like IronKey security certifications and other resources.
When you're done with a session, you click on "Lock", the Control Panel will go away and bring up the Unlocker. Simple as that. There are slight differences in operation and features between the different OS platforms, but for the most part functionality is the same.
Basic vs Enterprise version
The IronKey S1000 is available as a "basic" and an "enterprise" model. The terminology suggests that the enterprise version might be fancier, but it's really the same hardware. The difference is in the software.
 The enterprise software component ties individual IronKey flash drives into a secure cloud-based enterprise storage command center set up to administer and police the use of individual IronKey drives, or thousands of them. Interestingly, the IronKey Enterprise Management Services are handled by a different company, DataLocker. I am not getting into this part of the system, but it's clear that having central control and management of large numbers of encrypted secure mobile data storage devices is a very good idea. The enterprise software component ties individual IronKey flash drives into a secure cloud-based enterprise storage command center set up to administer and police the use of individual IronKey drives, or thousands of them. Interestingly, the IronKey Enterprise Management Services are handled by a different company, DataLocker. I am not getting into this part of the system, but it's clear that having central control and management of large numbers of encrypted secure mobile data storage devices is a very good idea.
Also note that Kingston offers a whole family of encrypted drives for customers of all levels who need their data protected to manage threats and reduce risks, all without slowly workflow or productivity (see Kingston's various lines of encrypted flash drives).
Kingston IronKey S1000 — for when security matters
It's not totally easy to review a product like the Kingston IronKey S1000. On the surface of it, it's just a USB key; you've seen one you've seen them all. But this is no ordinary USB key. The build, for one thing, is formidable. It's tough and rugged both outside and inside. It's dustproof and waterproof and definitely very rugged. But the IronKey is all about security.
Almost no one fully understands advanced details of cryptography. Kingston seems to employ all the state-of-the-art security technology available today. The all-important FIPS 140-2 Level 3 certification (as opposed to simply claiming to be "compliant") requires independent validation by one of the laboratories approved by the U.S. National Institute of Standards and Technologies (NIST). Kingston has that.
Flash drives providing this level of security are much more expensive than ordinary USB keys (IronKeys list from US$139 for 4GB, to US$849 for 128GB). Not having security and having something happen, however, is far more expensive.
-- Conrad H. Blickenstorfer, Editor-in-Chief, September 2017
Kingston IronKey S1000 product page page
Kingston Encrypted Devices page
Kingston security comparison page
DataLocker IronKey Enterprise Management Service page.
|


